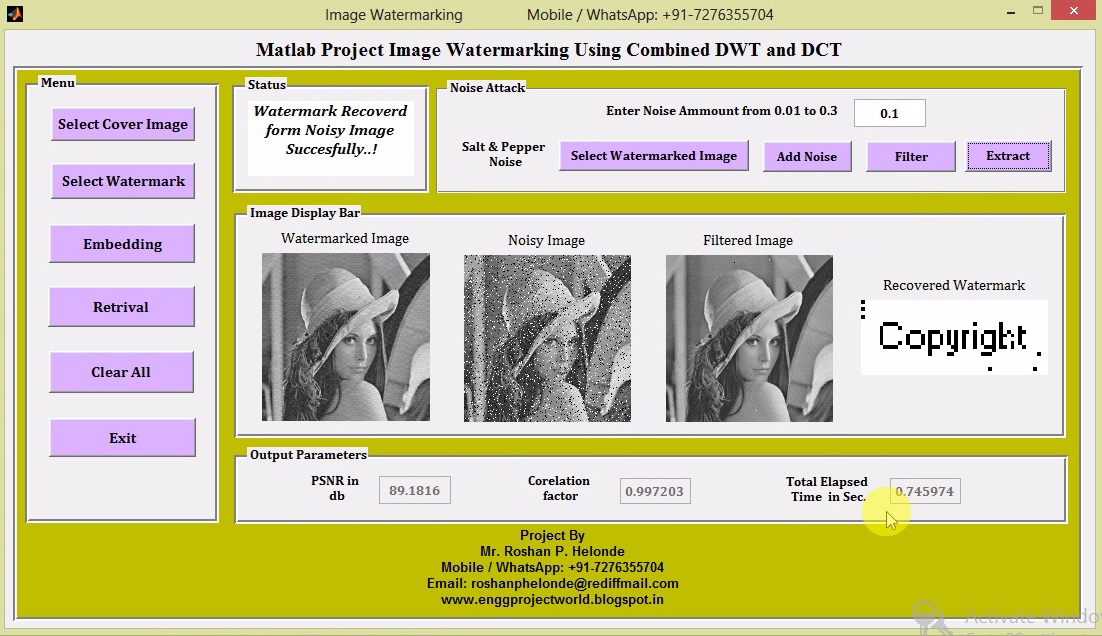
RECONSTRUCTION OF UNDERWATER IMAGE BY BISPECTRUM
DESIGN AND ANALYSIS OF BIT INTERLEAVED CODED SPACE-TIME MODULATION
CODING SCHEMES APPLIED TO PEAK-TO-AVERAGE POWER RATIO (PAPR) REDUCTION IN OFDM SYSTEMS
DETECTING DOMINANT MOTIONS IN DENSE CROWDS
A REAL-TIME ADAPTIVE LEARNING METHOD FOR DRIVER EYE DETECTION
DROP PARAMETER ESTIMATION FROM UNDERWATER NOISE PRODUCED BY RAINDROP IMPACT
EFFICIENT SPATIAL COVARIANCE ESTIMATION FOR ASYNCHRONOUS CO-CHANNEL INTERFERENCE SUPPRESSION IN MIMO-OFDM SYSTEMS
FAST AND EFFICIENT QOS-GUARANTEED ADAPTIVE TRANSMISSION ALGORITHM IN THE MOBILE WIMAX SYSTEM
DISCOV: A FRAMEWORK FOR DISCOVERING OBJECTS IN VIDEO
FUZZY LOGIC BASED EDGE DETECTION
FUZZY BASED PID CONTROLLER USING MATLAB FOR TRANSPORTATION APPLICATION
APPLICATION OF SUPPORT VECTOR MACHINE AND GENETIC ALGORITHM FOR IMPROVED BLOOD CELL RECOGNITION
DESIGN OF A DISTRIBUTED TRAFFIC MONITORING SYSTEM AND ALGORITHM BASED ON WEBCAMERA
AN IMPROVING MODEL WATERMARKING WITH IRIS BIOMETRIC CODE
AN EFFICIENT HARDWARE ARCHITECTURE FOR MULTIMEDIA ENCRYPTION AND AUTHENTICATION USING THE DISCRETE WAVELET TRANSFORM
A NEW STATISTICAL DETECTOR FOR DWT-BASED ADDITIVE IMAGE WATERMARKING USING THE GAUSS–HERMITE EXPANSION
A HISTOGRAM MODIFICATION FRAMEWORK AND ITS APPLICATION FOR IMAGE CONTRAST ENHANCEMENT
A MULTICODE APPROACH FOR HIGH DATA RATE UWB SYSTEM DESIGN
ULTRA-WIDE-BAND PROPAGATION CHANNELS
PERFORMANCE OF CDMA
OBJECT RECOGNITION USING EUCLIDEAN DISTANCE WITH KNN ALGORITHM
ROBUST IMAGE SEGMENTATION ALGORITHM USING FUZZY
PERSONAL AUTHENTICATION BASED ON IRIS TEXTURE ANALYSIS
A TOKEN-BASED SCHEDULING SCHEME FOR WLANS SUPPORTING VOICEDATA TRAFFIC AND ITS PERFORMANCE ANALYSIS
ADAPTIVE RADIO RESOURCE ALLOCATION FOR DOWNLINK OFDMASDMA SYSTEMS WITH MULTIMEDIA TRAFFIC
COOPERATIVE MIMO-BEAMFORMING FOR MULTIUSER RELAY NETWORKS
DUCHA A NEW DUAL-CHANNEL MAC PROTOCOL FOR MULTIHOP AD HOC NETWORKS
EFFICIENT POWER ALLOCATION FOR CODED OFDM SYSTEMS
MCMAC A PARALLEL RENDEZVOUS MULTI-CHANNEL MAC PROTOCOL
POWER ALLOCATION FOR TWO DIFFERENT TRAFFICS IN LAYERED MIMO SYSTEMS
SEMISOFT HANDOVER GAIN ANALYSIS OVEROFDM-BASED BROADBAND SYSTEMS
SEQUENTIAL DETECTION FOR MULTIUSER MIMO CDMA SYSTEMS WITH SINGLE SPREADING CODE PER USER
A MEDIUM ACCESS CONTROL SCHEME FOR TDD-CDMA CELLULAR NETWORKS WITH TWO-HOP RELAY ARCHITECTURE
A NEW PARAMETER FOR UWB INDOOR CHANNEL PROFILE IDENTIFICATION
VARIANCE-REDUCED PARTIAL PARALLEL INTERFERENCE CANCELLATION FOR MC-CDMA UPLINK SYSTEMS
MEASUREMENT BASED CHANNEL-ADAPTIVE VIDEO STREAMING FOR MOBILE DEVICES OVER MOBILE WIMAX
IEEE 802.16/WIMAX SECURITY
BIOMETRICS SECURITY IN WIMAX
DISTRIBUTED SUPPLY CHAIN MANAGEMENT USING ANT COLONY OPTIMIZATION
A CLOSED-FORM BLIND CFO ESTIMATOR BASED ON FREQUENCY ANALYSIS FOR OFDM SYSTEMS
BANDWIDTH EXCHANGE: AN ENERGY CONSERVING INCENTIVE MECHANISM FOR COOPERATION
EFFICIENT POWER ALLOCATION FOR CODED OFDM SYSTEMS
PERFORMANCE ANALYSIS OF DISTRIBUTED DECISION FUSION USING A CENSORING SCHEME IN WIRELESS SENSOR NETWORKS
NEURAL NETWORK BASED ENERGY EFFICIENT CLUSTERING AND ROUTING IN WIRELESS SENSOR NETWORKS
PERFORMANCE ANALYSIS OF MULTI-CARRIER DS-CDMA WIRELESS COMMUNICATION SYSTEM
SPEECH ENHANCEMENT USING HARMONIC EMPHASIS AND ADAPTIVE COMB FILTERING
A FAULT TOLERANT COMMUNICATION ARCHITECTURE SUPPORTING CRITICAL MONITORING WITH WIRELESS SENSOR NETWORKS
COOPERATIVE SENSING FOR PRIMARY DETECTION IN COGNITIVE RADIO
AUDIO CODING USING A PSYCHOACOUSTIC PRE- AND POST-FILTER
TIME-DOMAIN SIGNAL DETECTION BASED ON SECOND-ORDER STATISTICS FOR MIMO-OFDM SYSTEMS
· A Hybrid Time Divisioning Scheme for Power Allocation in DMT-Based DSL Systems
· A New Dual-Channel Mac Protocol for Multihop Ad Hoc Networks
· A Performance Study of Mobile Handoff Delay in IEEE 802.11-Based Wireless Mesh Networks
· Adaptive Routing in Dynamic Ad Hoc Networks
· Analysis of IEEE 802.11e for Delay Sensitive Traffic In Wireless Lans
· •
· Backup Path Set Selection in Ad Hoc Wireless Network using Link Expiration Time
· •
· Call Admission Control Optimization in Wimax Networks
· •
· Code Shift Keying Impulse Modulation for Uwb Communications
· •
· Contention-Based Qos Mac Mechanisms for Vbr Voip In Ieee 802.11e
· •
· A Medium Access Control Scheme for Tdd-Cdma Cellular Networks With Two-Hop Relay
· Architecture
· •
· A New Parameter for Uwb Indoor Channel Profile Identification
· •
· Novel Channel Interference Reduction In Optical Synchronous Fsk-Cdma Network using a
· Data-Free Reference
· •
· Performance Improvement in Wireless Networks using Cross-Layer Arq
· •
· Performance of Optical Burst Switched Networks for Grid Applications
· •
· Power Allocation and Scheduling for Ultra-Wideband Wireless
· •
· Networks
· •
· An Efficient Data Extraction Mechanism for Mining Association Rules From Wireless Sensor
· Networks
· •
· An FPGA-Based Architecture for Real Time Image Feature Extraction
· •
· An Improving Model Watermarking with Iris Biometric Code
· •
· Automatic Recognition of Exudative Maculopathy using Fuzzy Cmeans Clustering and
· Neural Networks
· •
· Reconstruction of Underwater Image by Bispectrum
· •
· Hierarchical Contour Matching for Dental X-Ray Radiographs
· •
· Robust Image Watermarking Based On Multiband Wavelets and Empirical Mode
· Decomposition
· •
· Image Segmentation using Iterative Watersheding Plus Ridge Detection
· •
· Real-Time System for Monitoring Driver Vigilance
· •
· Robust Dwt-Svd Domain Image Watermarking:Embedding Data in all Frequencies
· •
· Optimized Software Implementation of A Full-Rate IEEE 802.11a Compliant Digital Base band
· Transmitter on a Digital Signal Processor
· •
· Active Noise Cancellation with a Fuzzy Adaptive Filtered-X Algorithm
· •
· Design and Analysis of Bit Interleaved Coded Space-Time Modulation
· •
· Non-Symmetric Decompanding for Improved Performance of Companded ofdm Systems
· •
· Implementation of IEEE 802.11 a Wlan Baseband Processor
· •
· Signal Adaptive Subband Decomposition for Adaptive Noise Cancellation
· •
· A Performance Study of Mobile Handoff Delay in IEEE 802.11-Based Wireless Mesh Networks
· •
· Analysis of IEEE 802.11e for Delay Sensitive Traffic in Wireless Lans
· •
· Backup Path Set Selection in Ad Hoc Wireless Network using Link Expiration Time
· •
· Performance Improvement in Wireless Networks using Cross-Layer ARQ
· •
· Fingerprint Recognition System for FingerCode based
· •
· Face Recognition System
· •
· Speech Recognition System for isolated words
· •
· Recursive Gabor Filtering for 1D and 2D signals
· •
· Photorefractive Simulator System for calculating the vector space-charge field induced by
the Photorefractive effect.
DCT-based Watermarking for grayscale images
•
Wavelet-based Watermarking grayscale images
•
Iris Recognition System
•
Speaker Recognition System
•
Adaptive Equalizer
•
Advance Digital Signal Processing Graphics Compression
•
Audio Signal Processing
•
Channel Tracking using using Kalman Filter
•
Deriving Intrinsic Images from Image Sequences
•
Digit Recognition
•
Effect of equalization on a QAM based modulation scheme
•
Gesture Recognition
•
High Performance Implementation of MPEG-1 Layer 3 Audio
•
Human Hearing Threshold from EEG Signals using Neural Network
•
Image and Sound Compression using Wavelet
•
JPEG, motion compensation, MPEG-1, MPEG-2
•
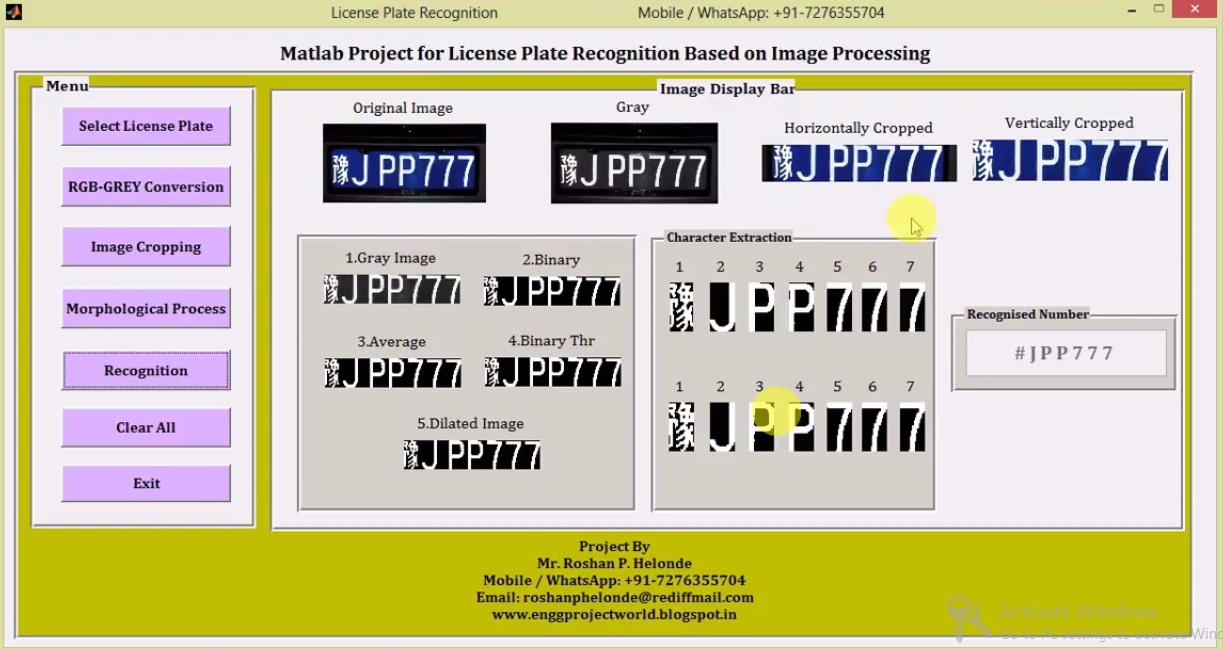
License plate Recognition / Number Plate recognition
•
Power Spectrum Estimation Periodogram & Modified Periodogram
•
Quadrature Amplitude Modulation (M-QAM Implementation)
•
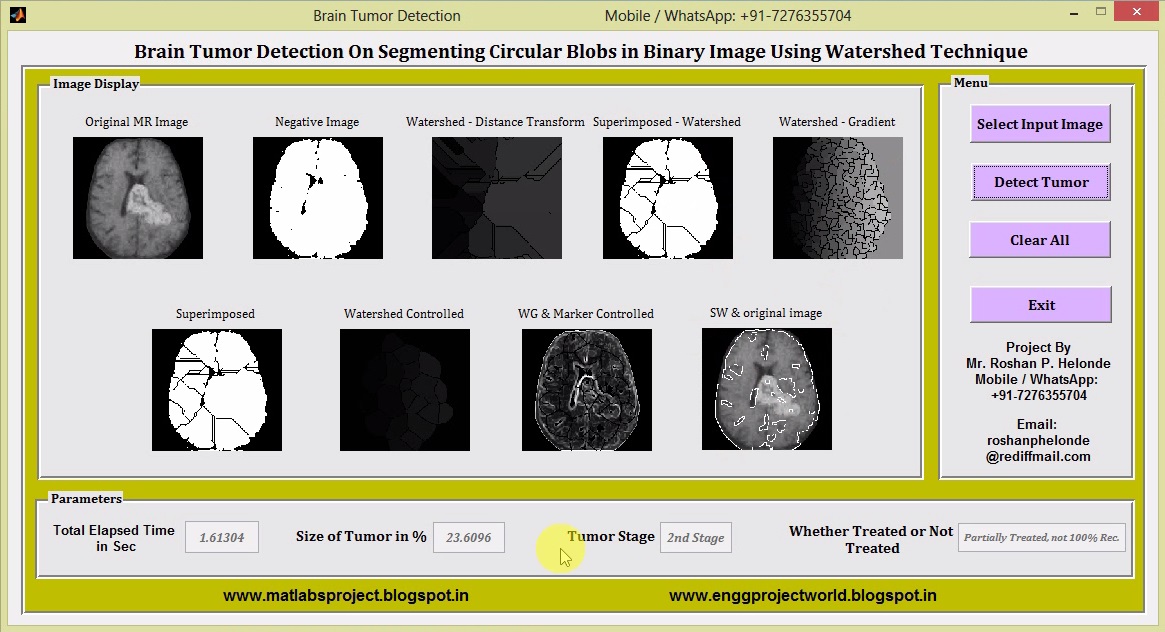
Recognition of Brain Tissues & Coloring of Magnetic Resonance Images
•
Coding of stereoscopic images - wavelet domain techniques
•
Compression, Predictive, Transform, Quantization
•
Car Thefts Detection
•
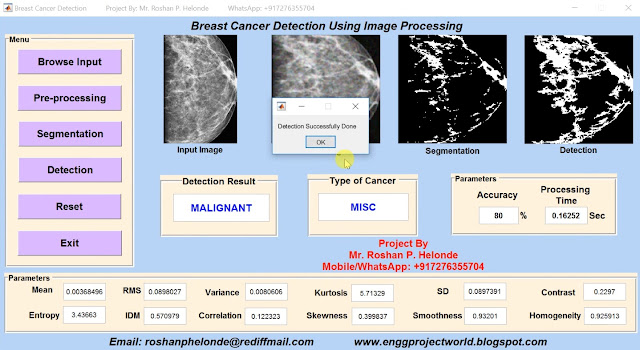
Content-Based Image Retrieval